Background
Yahoo was compromised in 2014 by a group of professional blackhats who were hired to compromise customer databases from a variety of different targeted organizations. Some of their initial targets, which occurred in 2012 and 2013, are linked directly with the recent large scale data breaches of social media networks and online-services such as MySpace, Tumblr and LinkedIn. Other well-known brands have been impacted by this group but the data stolen from them is not currently available for sale or validation in the underground, as of the writing of this report.
According to Andrew Komarov, Chief Intelligence Officer of InfoArmor, the nature of the identified data breach has a more “closed” character, due to the specifics of customers associated with this specific data and the motivations of the bad actors involved. Of significant importance, the Yahoo data leak as well as the other notable exposures, opens the door to significant opportunities for cyber espionage and targeted attacks to occur.
InfoArmor performed extensive analysis of collected intelligence surrounding the hack from a variety of sources in order to clarify the motivation and attribution of the key threat actors. As a result, it is clear that many recent press reports and published articles have significant inaccuracies.
Timeline Analysis
The first mention of Yahoo and a potential data breach appeared on cybercriminal forums immediately after the LinkedIn data was published for sale by the threat actor nicknamed “tessa88.”
03.04.2016 (3 April 2016)
tessa88, registered on several underground communities, was the first to mention that Yahoo account credentials were available for sale. According to operative sources and long term analysis, tessa88 acted as a proxy between the actual bad actors responsible for one of the largest hacks in history and potential buyers from various underground communities.
This approach was “carefully” orchestrated in order to mask the actual sources of the hacks and to commercialize the data in an anonymous manner, due to the fact that this data had been used by the threat actors for their own purposes, namely, targeted account takeover (ATO) and spam. Initially tessa88 proposed several databases for sale, including VK, MySpace, Fling and other notable e-mail providers and some instant messaging services from Eastern Europe. He initially mentions this data in a post, dated 11.02.2016 (February 2016), coinciding with the time frame when the data associated with the 2012 hacks was actually acquired.
In the interaction below, a record of the contact who engaged with tessa88 through operative channels, it is clear that tessa88 was not fully aware of the details surrounding the data he was selling. In some cases, this caused significant delays in data samples being shared.
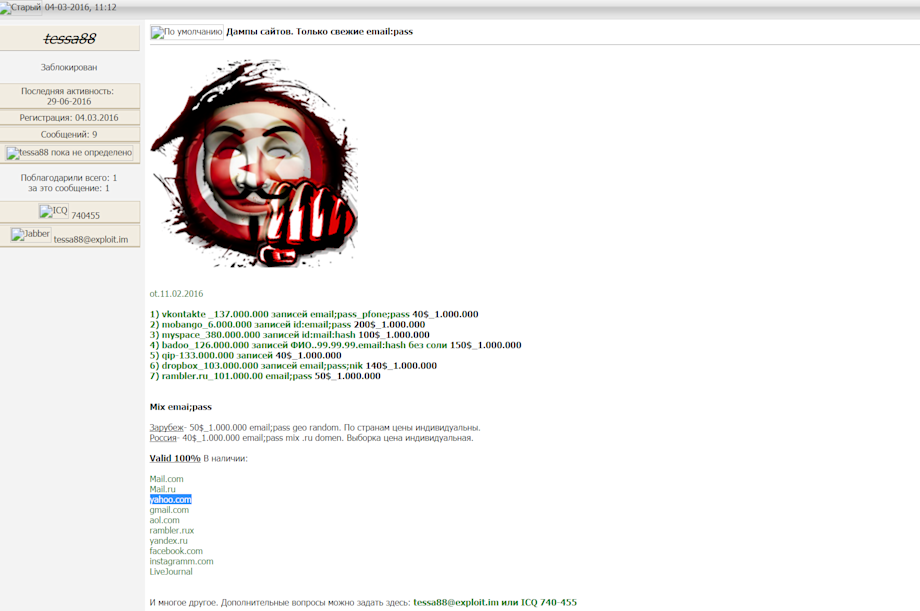
Translation
From 11.02.2016
Vkontakte (vk.com) 137 000 000 records; 40 USD per 1 000 000
Mobango 6 000 000 records; 200 USD per 1 000 000
MySpace 380 000 000 records; 100 USD per1 000 000
Badoo 126 000 000 records; 150 USD per 1 000 000 (email:hash without salt)
QIP 133 000 000 records; 40 USD per 1 000 000
Dropbox 103 000 000 records; 140 USD per 1 000 000
Rambler 101 000 000 records; 50 USD per 1 000 000
Mix email:pass
Other countries – 50 USD per 1 000 000 records, email:pass, individual pricing per geography
Russia – 40 USD per 1 000 000 records, email:pass mix, .ru domains, individual parsing
Valid 100%
Mail.com Mail.ru Yahoo.com Gmail.com AOL.com Rambler.ru Yandex.ru Facebook.com Instagramm.com Livejournal.com
And many other things. With questions – tesssa88@exploit.im, or ICQ 740-455
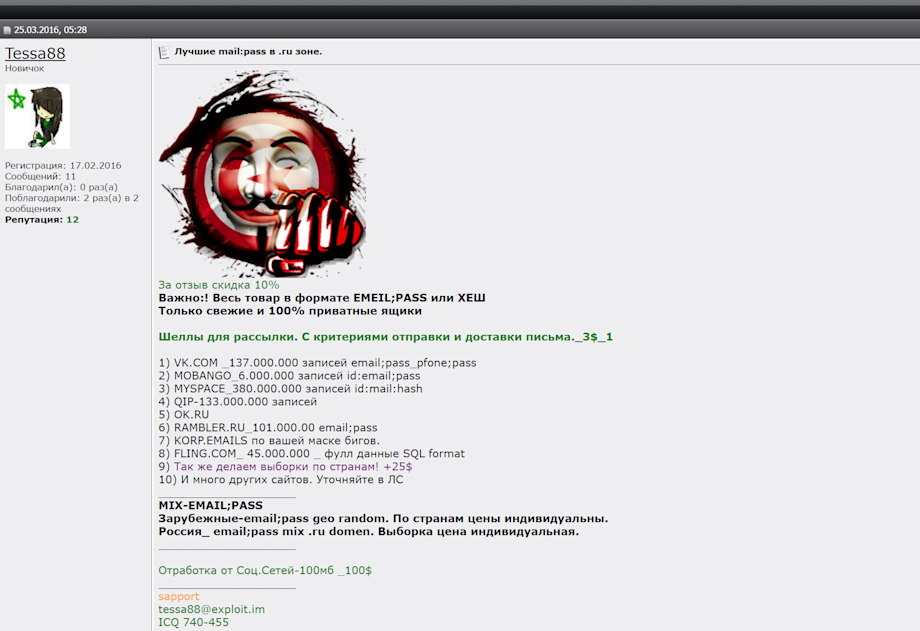
Translation
Important! All my stuff is in the following format EMAIL:PASS or HASH
Only fresh and 100% private mailboxes
WEB-shells for spam.With criteria for sending. 3 USD / 1
VK.COM 137 000 000 records, email:pass
MOBANGO 6 000 000 records, id:email:pass
MySpace 380 000 000 records, id:mail:hash
QIP 133 000 000 records
RU
ru 101 000 000 records email:pass
EMAILS (Business E-Mails) by your criteria
COM 45 000 000 records, full SQL format
Individual parsing by your country +25 USD
Many other WEB-sites. Contact me in PM
MIX-EMAIL:PASS Other countries (email:pass, geo random). Individual prices per country. Russian (email:pass mix .ru). Individual criteria for parsing.
Social Networks 100 MB – 100 USD
Support
01.05.2016 (01 May 2016)
The actor “Peace_of_Mind” (PoM), well known for his activities at “The Real Deal Market” (TRDM) and “The Hell” forum, after identifying his post regarding the stolen data at one of the underground forums, contacts tessa88 and proposes some sort of cooperation [partnership] in exchange for some of his data.
Subsequent to this engagement, the databases initially published for sale by tessa88 are then resold by Peace_of_Mind in TOR network at TRDM. This is an interesting example of cooperation between a Russian speaking threat actor and an English speaking actor, demonstrating that cybercrime is an entirely transnational issue.
14.05.2016 (14 May 2016)
Peace_of_Mind outlines that he will share the data dumps of Mate1.com, Zooks.com, Lbsg.net, r2games.com and several other hacked WEB-resources, all having large user populations, with tessa88. At this point, tessa88 updated his initial thread on the underground forums with these resources and adds LinkedIn for the first time in the list of the stolen databases available for sale.
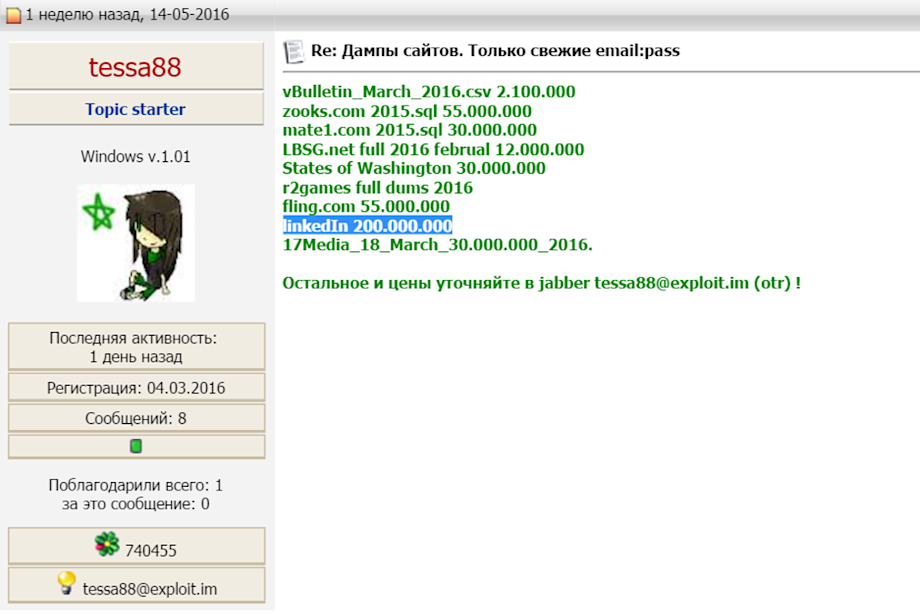
Peace_of_Mind, now acting as a partner with tessa88 in the compromised data exchange, immediately reposts the acquired databases from the initial tessa88 list at TRDM in TOR network under his own nickname.

Presumably, this action creates the first conflict between these supposed partners, as tessa88 has never discussed monetization of his data without his permission in an uncontrolled way. Peace_of_Mind also makes claims regarding tessa88, as he determined that some of the acquired data was misrepresented or falsified, not including any additional information regarding successful decryption of hashes and/or having absolutely no relationship to resources he was claiming had been exposed.
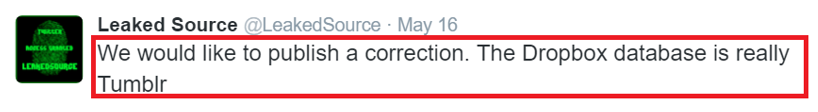
For example, “LeakedSource,” another partner of tessa88 acquired the same data through the chain of proxies and mentions that the published Dropbox dump for sale is actually Tumblr.
10.06.2016 (10 June 2016)
The actor “InstallsBuyer” creates a blacklist[1] including tessa88, at which point tessa88 is banned on many underground forums. The reason for blacklisting tessa88 is because of the delivery of fake and low quality data provided to some of the buyers on this site (claimed VK, MySpace, Twitter dumps, specifically).
The author of the blacklist mentioned that he had sent tessa88 10 BTC (~ 6021.40 USD) and was not able to recover them. This fact raised questions about the competence of tessa88. However, inconsistencies regarding legitimacy were further compounded, since the LinkedIn data as well as the data from several other compromises provided by tessa88 was valid.
01.08.2016 (01 August 2016)
The actor Peace_of_Mind (PoM) published the data from the alleged “Yahoo dump” at the well-known underground marketplace “The Real Deal Market” (TRDM) in TOR network.
[1] https://forum.exploit.in/index.php?showtopic=104679

Unfortunately, the security community and press haven’t verified the dump and appear to be focused only on the significant number of records having @yahoo.com domain name. For any experienced threat intelligence analyst, the price of 3 BTC (~ 1806.42 USD) for 200,000,000 Yahoo user accounts is suspiciously strange and has no rational explanation.
Further, by evaluating a sample of records, more confusion is created because the decrypted passwords from some of them were legitimate for actual Yahoo users. However, the vast majority of the data is not legitimate, including invalid accounts, deleted accounts, and nonexistent accounts. After extensive analysis and cross reference against the data breach intelligence systems of InfoArmor, it was determined that the dump is based on multiple third party data leaks, which have no relation to Yahoo. Presumably, the threat actor specially misrepresented this data set in order to sensationalize and sell it for the purpose of monetizing his efforts following the negative impact of his relationship with tessa88.
Since individuals reuse exactly the same passwords for multiple online-services, some low level of positive conversion rate is inevitable, making ATO possible with a very small number of user accounts and may explain the positive validation of this limited number of accounts.
According to discovered information, both bad actors expected to receive the actual Yahoo dump under set conditions from the real hackers that the data will be monetized in an efficient and careful manner; however, this did not happen. It is possible that the activities of both actors may explain the heavy wave of recent DDoS attacks on “The Real Deal Market.”
Perpetrators Analysis Graph
As a result of InfoArmor’s analysis, two different groups are clearly identified:
Group 1 (“Hell Forum” members - group of English speaking threat actors) (red)
Group 2 (“Group E” members - group of professional blackhats from Eastern Europe) (green)
Both groups of threat actors are noteworthy and act globally, but only Group 2 has any direct relation to Yahoo hack in 2014. Group 1 is notable because of their key member, “ROR[RG],” who has previously hacked Ashley Madison, AdultFriendFinder and the Turkish National Police database. This activity opened the door into the spring of large scale data breaches that have occurred over the past several years, which has surprised the security community.
The fundamental linkage between these two groups is through a proxy with tessa88, the threat actor who is reselling the LinkedIn dump, along with several other data dumps. It appears that tessa88 has been the focus of due diligence and evaluation by these groups for some period of time. This relationship continues to develop as monetization strategies are developed.
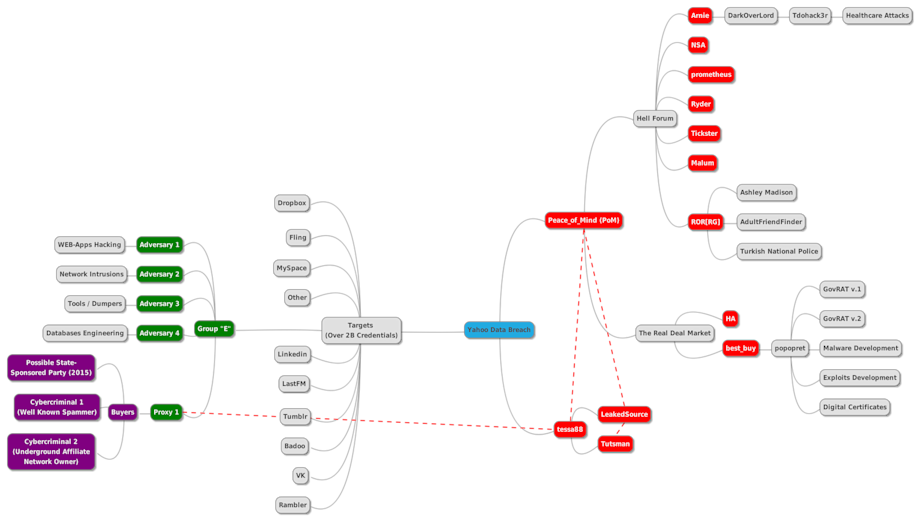
The proxy was also responsible for the initial sale of specific stolen data to interested parties in 2015. We determined, that one of the first deals occurred with a state-sponsored party who had interest in exclusive database acquisition. Two other transactions took place with notable cybercriminals who planned to use the data for spam campaigns against global targets, monetizing their activities through their own underground affiliate networks.
Several targets, aside from Yahoo, are still unconfirmed and unverified. This has led to several online-services making broad statements denying any data leaks. This can be seen in two cases where tessa88 shared databases without any additional “salt” information, which is required for successful password recovery.
Yahoo Data Breach – What The Real Dump Looks Like?
Evaluating the Peace_of_Mind claims regarding 200,000,000 compromised users, the actual stolen database includes potentially 500,000,000 Yahoo users, provided in the following structure:
Yahoo login (ID);
Country Code;
Recovery E-Mail (Linked with the profile);
Date of Birth (DOB);
Hash of Password (MD5);
Cellphone and ZIP code (if it was provided by the user for password recovery).
According to InfoArmor’s intelligence, the bad actors exfiltrated the data in segments which is supported by the fact that the database dump is divided into over a hundred equal parts, delivered in different files that are organized alphabetically by the name of user accounts.

The actual Yahoo data dump is still not available on any underground forums or marketplaces, and has been distributed from so called Group “E” to one of their proxies for further monetization based on the sale of particular records from the dump, which can be delivered based on the specific criteria of the buyer (login, recovery e-mail, geography, etc.).
According to InfoArmor, the data theft of the Yahoo customer database may be the key in several targeted attacks against US Government personnel, which resulted after the disclosed contacts of the affected high-level officials of intelligence community happened in October 2015. It should be noted that after the LinkedIn breach, the company acted proactively by notifying their subscriber base and implementing new security measures to avoid further incidents.
InfoArmor recommends that the Security Community use appropriate due diligence in evaluating any threat actor claims regarding legitimate data sources. Given the nature of the relationships between threat actor groups, proxy organizations and parsing of data, as shown above, enterprises, agencies and individuals are encouraged to be on high alert for espionage, infiltration, and impersonation. InfoArmor will continue to monitor this situation and provide further updates as pertinent information becomes available.
At InfoArmor, we believe everyone deserves the right to privacy, security, and above all else, peace of mind. This is why we’re proud to offer industry-leading solutions for employee identity protection and advanced threat intelligence. From enterprise to employee, InfoArmor redefines how organizations combat an ever-changing cyber threat landscape. If you’d like more information on how we can help your organization protect its most valuable assets, reach out. We’d love to hear from you.


