In early March 2016, the InfoArmor Threat Intelligence Team investigated several targeted cyber-attacks against select US-based healthcare institutions. The bad actors are claiming that they have exfiltrated more than 3TB of data that contain sensitive PII that clearly distinguish the patients along with other confidential medical data.
According to InfoArmor’s Chief Intelligence Officer Andrew Komarov, all of the identified attacks reflect similar attack vectors. These malicious attacks were accomplished by intrusion into the network through weak remote administration channels that exfiltrated additional data from network segments that shared converged connections with other medical devices.
At the end of June 2016, the bad actors published 10,000,000 stolen record for sale. Previously, the main threat actor has changed his nickname several times from “Arnie” to “The Dark Overlord.”
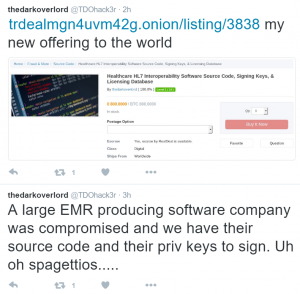
On July 12, 2016, the threat actor published on his Twitter page (https://twitter.com/TDOhack3r) that he is selling stolen source code of one of the well-known EMR (electronic medical records) software along with the private keys (for code-signing).
In early March 2016, the InfoArmor Threat Intelligence Team investigated several targeted cyber-attacks against select US-based healthcare institutions. The bad actors are claiming that they have exfiltrated more than 3TB of data that contain sensitive PII that clearly distinguish the patients along with other confidential medical data.
According to InfoArmor’s Chief Intelligence Officer Andrew Komarov, all of the identified attacks reflect similar attack vectors. These malicious attacks were accomplished by intrusion into the network through weak remote administration channels that exfiltrated additional data from network segments that shared converged connections with other medical devices.
At the end of June 2016, the bad actors published 10,000,000 stolen record for sale. Previously, the main threat actor has changed his nickname several times from “Arnie” to “The Dark Overlord.”
On July 12, 2016, the threat actor published on his Twitter page (https://twitter.com/TDOhack3r) that he is selling stolen source code of one of the well-known EMR (electronic medical records) software along with the private keys (for code-signing).
In his post he mentioned:
Listed here is the source code, signing keys, and licensing database stolen from a large HL7 software developer located in the United States. This HL7 software has been distributed and used by hundreds of clients around the world. This software allows an organization to link hundreds of healthcare devices and databases together to help mitigate the cost of purchasing newer software products and expanding the life span of healthcare systems through the use of its integrated development environment that can be used to generate new assembly line style automation of processes and data transfer. In addition to the source code for the HL7 Interface Engine software, the private keys for signing the code will also be included as well as the licensing database that entails a full record of all clients and their deployment and status information.
Health Level-7 or HL7 refers to a set of international standards for the transfer of clinical and administrative data between software applications used by various healthcare providers. These standards focus on the application layer (Layer 7) in the OSI model. The HL7 standards are produced by Health Level Seven International, an international standards organization, and are adopted by other standards issuing bodies such as the American National Standards Institute and International Organization for Standardization. Hospitals and other healthcare provider organizations typically have many different computer systems that are used inclusively from billing records to patient tracking.
Click here to download the Intelligence Report – Healthcare Under Attack.


