Identity Theft Awareness Week: identity theft’s hidden impact
5 min
You know your company needs identity theft protection.
You know the risks. You know the benefits.
But it’s not like you can just march into your next strategy session and say, “We need this!”
You need to have your facts straight.You need to have your talking points.
You need to have a plan.
That’s what this report is for. To help you frame a discussion with your partners in the C-suite, such as the CEO and CFO.
To help convince them what you already know: Your organization needs identity theft protection, and the sooner the better.
So here’s what we’re going to cover:
Part 1:High Level Costs and Trends
Part 2:Types and Definitions of Protection
Part 3:Legal Concerns
Part 4:Corporate, Health and Financial Impacts
Part 5:Core Elements and Key Differentiators
Part 6:Voluntary vs. Employer-Sponsored
According to Javelin’s 2019 Identity Fraud Study, 14.4 million consumers were victims of identity fraud in 2018alone.
While this is a drop from 16.7 million victims in 2017, it also may reflect a shift in cybercriminal tactics. Due mainly to the adoption of EMV chips, traditional non-cash frauds such as ATM, pay-at-the-pump, and wireless card-skimming are on the decline. Instead, fraudsters have been seen targeting larger scores such as account takeovers and new account creation.
New account fraud is when a new account is opened using all or part of someone else’s personal data. Mortgages, student loans and car loans are just a few of the big ticket accounts targeted here. Total losses from these frauds rose from $3 billion to $3.4 billion in 2018.
Account takeovers are when cybercriminals gain access to someone else’s account and seize control. Many cell phones, for example, have automatic access to emails, social media, shopping and even financial accounts once the initial security is bypassed. Cell phone takeovers almost doubled in 2018, from 380K to 679K known incidents.
Similarly, while the overall number of known security breaches dropped by 23% in 2018, the Identity Theft Resource Center noted that cybercriminals were after more damaging — and valuable — information. Despite the number of breaches and the number of consumers victimized both dropping in 2018, the number of consumer records containing personally identifiable information (PII) skyrocketed from 197.6 million to 446.5 million.
Yes, cybercriminals seem to be getting smarter. And that’s bad news for all employers.
Because those consumers are also your employees. A breach at your company will, very possibly, expose them. But so might a breach at Facebook. Or a breach at Equifax. Or a breach at Marriott.
When it comes to your employees, it doesn’t matter as much where the information was stolen. What matters is that employees dealing with identity theft fraud may, understandably, be distracted. As the severity and scale of these thefts continue to climb, so can their levels of distraction. By the same token, the more employees exploited by identity theft, the greater the impact may be to your business as a whole.
Gallup’s State of the American Workforce reported the costs of an average distracted employee as:
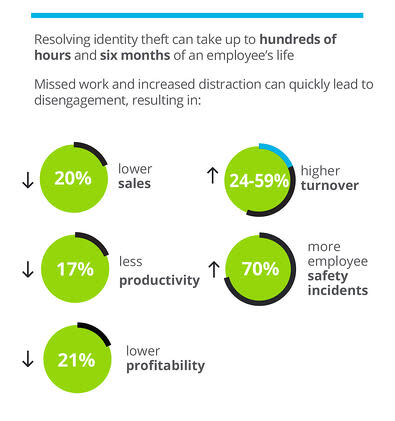
The risks are plain to see. Hardening your cybersecurity may reduce the likelihood of a breach at your company, but it can’t protect your employees from all the other sources of exposure. So one way to help protect your safety, productivity, sales, profits and turnover rate from the risk of identity theft is with identity theft protection.
“You say to-may-to, I say to-mah-to.”
Getting everyone on the same page for an identity theft protection discussion could be one of your first challenges. That’s because many of the necessary terms are buzzwords… meaning the words that are most often used are new and may not be clearly defined.
Use this simple guide to minimize any miscommunications in your discussions that are due simply to the terminology.
Data Privacy: The conditions — such as who, when, where — under which data can be accessed; it can include both internal rules as well as external laws and regulations
Data Security: The measures used to protect data from unauthorized access, both in general and to support data privacy
Data Breach: Any unauthorized viewing, access, or retrieval of data
Compromised or Exposed Data: Any piece of data which has been viewed or accessed without proper authorization
Stolen Data: Compromised data which is actually retrieved, copied, or stored
Fraud: Any deception intended to result in personal or financial gain
Identity Theft: A type of fraud where stolen data is used to create, access, or manipulate new or existing accounts and/or records of the original owner
Credit Protection: A form of protection where credit reports and scores are monitored for inaccurate or suspicious activity, these are sometimes combined with corrective tools to help users fix credit problems
Identity Theft Protection: Taking privacy protection a step further, this is a form of protection which often includes monitoring of external sites for signs of compromise, as well as offering a variety of recovery measures when an identity theft occurs
Beyond these basic definitions, how each protection program defines words like “monitoring” and “family” and “insurance” will have a great impact on its overall value and effectiveness. We’ll discuss these terms in Core Elements and Key Differentiators below.
We all know the power of legal and regulatory compliance when it comes to making business decisions. With regards to privacy and identity theft, there have been several high profile cases and news items lately that may warrant a discussion with your legal team.
Even now, without tight regulations on data privacy in the U.S., many incidents have led to major fines.
Earlier this month (July 2019), the FTC approved a record $5 billion settlement with Facebook for its treatment of user privacy data. Their investigation was triggered by the well-documented Cambridge Analytica scandal but pointed to many other instances where data may have been mishandled. One very important side note is that there have been internal FTC discussions about whether Facebook CEO Mark Zuckerberg should be held personally accountable. As of this writing, that question has not been answered, but the fact that it is — or was — being discussed may be relevant to your C-suite.
Also this month, the FTC approved a multimillion dollar settlement with Google for violating the Children’s Online Privacy Protection Act. They determined that Google improperly collected child data through its YouTube service and also stated it did not adequately protect that data.
And also this month, the FTC approved a settlement of up to $700 million with Equifax over its 2017 breach. This includes cash payments of up to $20,000 for each person adversely affected by the breach.
As you can see from these three high-profile and very recent cases, the FTC is taking data privacy extremely seriously. Much tighter regulations to help them control the situation could be on the horizon.
Internationally, the European Union’s General Data Protection Regulation (GDPR) went into effect just over a year ago. This could serve as a framework for future U.S. regulation, but it directly impacts any business collecting data from European Union members right now. France’s CNIL issued the first major court decision involving GDPR violations — against Google — but EU regulators are just warming up, calling 2019 a transition year.
Back in the U.S., state and local courts were some of the first to hear and issue rulings on privacy violations.
In the recent landmark decision, Dittman vs. UPMC, the Pennsylvania Supreme Court ruled that because the University of Pittsburgh Medical Center (UPMC) collected and stored sensitive employee data, it had an obligationto provide adequate security measures to keep that data safe. When an external hack compromised the data of more than 62,000 employees, the court determined that UPMC did not adequately protect that data and were therefore responsible for the theft.
On the state legislature side, the California Consumer Privacy Act (CPA) takes a stance similar to the GDPR. While each state has its own laws governing data breaches, the CPA is the toughest litmus test in the U.S. to date when it comes to assessing the responsibility for companies to protect data privacy. While it doesn’t take effect until January of 2020, it may impact not only California businesses, but all companies doing business with them and on the internet…and most U.S. companies are not ready for it.
All this goes to show that the legal situations governing privacy and online fraud are complex. Actions can come from several different quarters:
From employees: either those affected by a breach of your organization, or those seeking recompense for time, wages, and even jobs lost due to dealing with an identity theft
From consumers: if a breach is traced back to your company, you might be held liable if sufficient safeguards were not in place
From vendors: if hackers use a breach at your organization to infiltrate accounts at your clients, suppliers, or other business partners, you could also be held liable
From governments: federal, state, local, and even international governments have all issued rulings on identity theft cases that hold companies liable for not protecting the data privacy of their employees and consumers
Your legal team is best suited to help you navigate through these new developments. They can also help you determine how a potential identity theft solution might impact your own risks and exposures.
We discussed the high level trends of identity theft above. But what are some other ways offering an identity theft benefit have been known to impact a company’s bottom line?
As you’ve no doubt noticed, breaches often open PR and marketing challenges for the companies involved. An identity theft protection benefit can help alleviate some of those costs by reducing reputational damage from a breach.
While identity thefts in your workplace can increase your employee turnover rate, offering a great benefits package can not only reduce turnover, but also attract better talent.
It turns out that concerns of identity theft are high in the American mindset. One survey conducted in the U.S. found that criminal hacking was ranked as the number one threat to American health, safety and prosperity. Meanwhile, the FTC has reported identity theft as one of the top three consumer complaints for five straight years.
With recognition so high, it should come as no surprise that employees may want protection. BenefitsPRO named identity theft protection as one of three cornerstone benefits continuing to trend up in 2019. And Forbes listed it as one of their 5 Unconventional Job Benefits to Attract and Retain Top Employees.
On the healthcare front, reducing stressors in your workplace can have positive effects on the overall health and engagement levels of your workforce.
Regarding security, identity theft protection can complement your cybersecurity measures for a more thorough solution. Here are some ways the top providers can improve your overall corporate security:
Providing ongoing education and updates for the latest identity theft tactics and risks
Protecting your employees’ social media accounts
Protecting corporate credit cards, usernames, and passwords
Monitoring dark web activity for any trace of your company or employee data
Now, let’s put some numbers from the Identity Theft Resource Center’s (ITRC) Aftermath studies to quantify some of the struggles faced by individual employees:
On average, an identity theft case takes 100 to 200 hours to remedy. That’s roughly 12 to 25 full workdays lost of their wages and/or benefits as well as your productivity.
The average duration for resolving an identity theft, from submitting a claim to finalizing paperwork, is about six months. Add the time between discovery of the problem and submitting a claim, along with the time afterwards while the out-of-pocket costs are being reconciled into budgets, and you’ll get the length of time during which an employee is working in a “stressed” condition.
The average out-of-pocket costs are $1500.
And these are just the “average” numbers. Some identity theft cases take years to unravel and cost tens of thousands of dollars. The average out-of-pocket costs for a medical record identity theft, for example, is $22,346.
Knowing the range of benefits an identity theft protection program can offer may also support the success of your C-suite discussion. In this section, we’ll discuss some of the core coverages and protections being offered and what they mean. We’ll also cover a variety of differentiators — features that set one program apart from another — because the range of offerings may be so great that choosing the right solution may be just as important as your decision to adopt one.
All identity theft protection packages may claim to monitor one or more of the following:
Credit report monitoring
Credit-based account monitoring
Social media monitoring
Dark web monitoring
Credit report monitoring looks at credit reports and score changes whenever they’re published. The goal is to identify events which moved scores in a negative direction and verify with the customer that those events were legit.
Credit-based account monitoring scans those accounts which impact your credit score the most: banking, credit cards, investments, etc. It looks for suspicious activity as well as financial errors. Potential problems include duplicate charges, failed login attempts, unusual purchase behaviors and geographic anomalies. Which activities they scan for and how they do it is a prime example of a differentiating factor, so it’s good to know what your monitoring software is capable of.
Social media monitoring looks for the signs of hacking your social media accounts. Account takeovers are one of the main threats here. Best-in-class social media monitoring will also let you scan your account for vulgar and explicit language, violent or threatening messaging, and potentially damaging content. Again, what each solution provider calls “social media monitoring” can vary greatly, so compare the details before deciding.
Dark web monitoring involves searching the dark web for signs of hackers selling breached data to thieves. Searching for National Provider Index numbers (NPI) is one way to do this. The problem — and why many identity theft solutions only offer “scanning” — is that it’s not possible to accomplish with automated scans alone. Due to the nature of the dark web’s infrastructure and the secretiveness of the thieves, dark web monitoring is a labor intensive process reliant on human agents and not just bots.
This may be another huge differentiator within the identity theft protection industry. Recovery has shown to directly impact the stress levels of employees dealing with identity theft. One reason is that restoring their identities may necessitate out-of-pocket costs, which some employees may not have. So a comprehensive recovery insurance policy is crucial to holistically caring for employees post-breach, regardless of their financial situation
At its most basic, recovery insurance covers the costs associated with an identity theft recovery. These can include filing fees, claim fees, statement requests, postage, etc.
A slightly better solution may or may not cover additional costs such as: legal fees, out of work costs, emergency quality of life funds, etc.
And in the very top tier of identity theft protection solutions are the few that actually replace stolen funds — regardless of whether they can eventually be recovered.
The problem is that all of these levels of protection, from basic to top tier, can be labeled as “identity theft recovery insurance.” But you can plainly see the differences once you know what to look for — and so can your employees.
And while many home insurance policies list identity theft as a covered benefit, they may cap the damages at values as low as $500. Remember that the average out-of-pocket costs were $1500?
Compare that to an average identity theft recovery plan that covers up to $15,000 (being careful to note this amount has nothing to do with what types of expenses are covered) — which is still short of the average medical record identity theft cost of $22,346.
Another key differentiator is how your identity theft benefits provider defines family. Because while many identity thefts occur when PII from corporate breaches lead to hacked personal accounts, the same can be said the other way around.
How your identity theft benefits provider defines and covers family may have an impact on the amount of risk your workplace is exposed to from their households.
Customer service levels, education, and other protective features such as secure digital wallets and two-factor authentication on personal accounts can all provide differentiation between solutions, too.
Identity theft protection benefits both company and employee, so including it as part of your voluntary employee benefits package makes sense.
Offering it as a benefit also provides several advantages:
Gives visibility to the issue
Shows the company is endorsing a solution to the identity theft problem
Provides a "platform" for the company to share privacy and identity theft related news and updates, even if the employee doesn't opt-in to the actual service
Forces a decision
That last point is critical. Even if they choose not to elect some form of privacy protection, you've made them think about the issue. This in itself may lead employees to be more sensitive to data privacy issues and to make better decisions involving their data security.
You’ll also likely need to discuss with your C-suite the employee subscription rates you’ll want to target. This is dependent on what percentage of the subscription costs will be paid by your company versus by the employee. Here you have three options:
Fully company funded with no additional cost to the employee
Partially subsidized, where the company pays a designated portion and the employee pays the remainder
Fully employee funded with the full subscription cost passed through to the employee
Fully funding ensures all your employees will be covered. This helps minimize the potential costs of identity theft established above for both the company and its employees.
Subsidizing lowers your company’s share of the benefit, but also lowers the subscription rate.
Passing the cost on to your employees offers the lowest up-front cost for your company, but also may result in the lowest subscription rate.
With some solutions, you’ll also have options to “buy-up” to better, broader, or more comprehensive plans. Family coverage is one such option, and here your choices are similar: employers can fund it fully, subsidize a portion of the cost, or pass the full family upgrade cost on to the employee. Different levels of protection, insurance, and support might also fall into the voluntary vs. employee-sponsored discussion.
You’ll need to perform your own ROI assessment to determine what level of voluntary vs. sponsored makes the most sense for your organization. While some of the costs of identity theft are easily quantifiable, others — such as reduced legal exposure, reputational damage, and the positive impacts of protected employees — are much less so.
Identity thieves may target everyone. No individual, business or industry is fully safe. But the type of information targeted and how it’s obtained can vary greatly. For the most up-to-date statistics and analysis specific to your industry, check out our Ultimate Industry by Industry Guide to Identity Theft.
You may want to share those details in your discussions as well.
All the breaches you read about above, as well as in the news, do not only occur at companies with lax cybersecurity measures. Some of them are cutting edge. But the tools and resourcefulness of some cybercriminals are, too. And then there are those who get help from the inside. So while no security can ever guarantee you 100% against a breach, identity theft protection can help you minimize the damage.
Now it’s up to you to persuade your organization to make that change.
If you’d like more information like this to help convince your C-suite that the time to act on identity theft protection is now, give us a call. We’d be glad to assist in keeping you and your employees safe from the growing costs of identity theft.
If you're considering one of our services, want more information, or need assistance, please reach out. We’re here to help.